Network Security: Hill Cipher (Decryption)
Topics discussed:
1) Classical encryption techniques: Substitution and Transposition techniques.
2) Introduction to the basics of Hill cipher.
3) Mathematical concepts to be known in order to deal with Hill cipher encryption and decryption problems.
4) The Hill Algorithm – Encryption and Decryption process of Hill cipher with expressions.
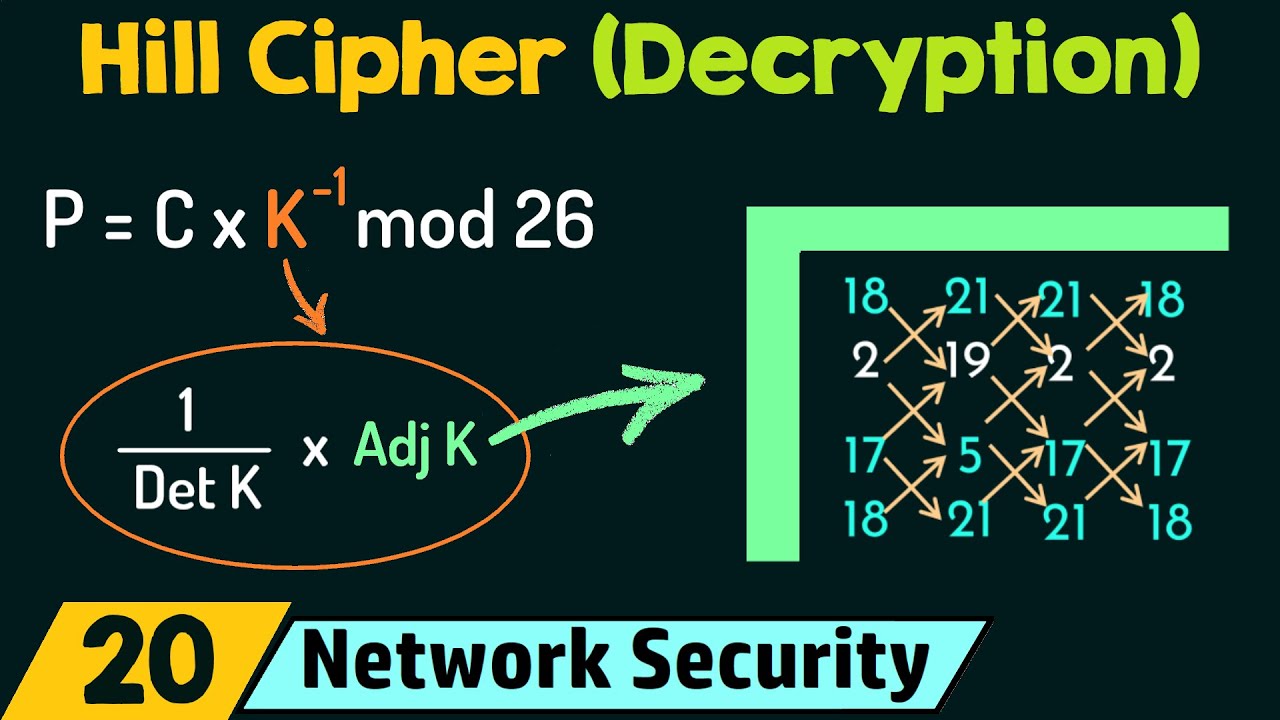
5) Formula for finding the key inverse matrix and explanation of all the parameters involved.
6) Example – Decryption using Hill cipher for the plaintext “RRLMWBKASPDH” with a 3×3 Key Inverse matrix.
7) Finding the determinant of a 3×3 matrix using a short-cut approach.
8) Finding the adjoint of a 3×3 matrix using a short-cut approach.
9) Finding the multiplicative inverse of a number with modulus.
10) Verifying the key inverse matrix.
11) Information about square matrix and unit/identity matrix.
12) Various ways of doing Hill cipher encryption and decryption using Row Vector approach and Column vector approach.
Follow Neso Academy on Instagram: @nesoacademy (https://bit.ly/2XP63OE)
Contribute: http://bit.ly/3EpZgBD
Memberships: https://bit.ly/2U7YSPI
Discord: https://bit.ly/3HiGtJr
WhatsApp: https://whatsapp.com/channel/0029Va9B1Bq4tRru0nqgtx3h
Books: https://bit.ly/4cZYQil
Website ► https://www.nesoacademy.org/
App ► https://play.google.com/store/apps/details?id=org.nesoacademy
Facebook ► https://www.facebook.com/nesoacademy
Twitter [X] ► https://x.com/nesoacademy
Music:
Axol x Alex Skrindo – You [NCS Release]
#NetworkSecurityByNeso #Cryptography #NetworkSecurity #HillCipher


Comments