 テクノロジー
テクノロジー Fully Homomorphic Encrypted Facial Recognition with TenSEAL in Python
In this video, we explore the implementation of fully homomorphic encryption (FHE) for facial recognition using the De...
 テクノロジー
テクノロジー 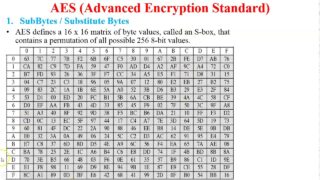 テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー