 テクノロジー
テクノロジー ランサムウェアによって暗号化されたデータを復元する“世界初”のツール 警察庁サイバー特別捜査部が開発|TBS NEWS DIG #shorts
警察庁はきのう、特定の身代金要求型ウイルス「ランサムウェア」によって暗号化されたデータを復元するツールを世界で初めて開発したと発表しました。
企業の機密データを暗号化する身代金要求型ランサムウェア「Phobos」や「8Base」による...
 テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー 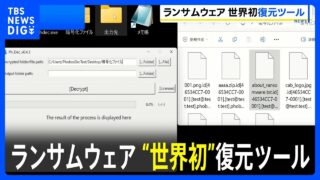 テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー  テクノロジー
テクノロジー